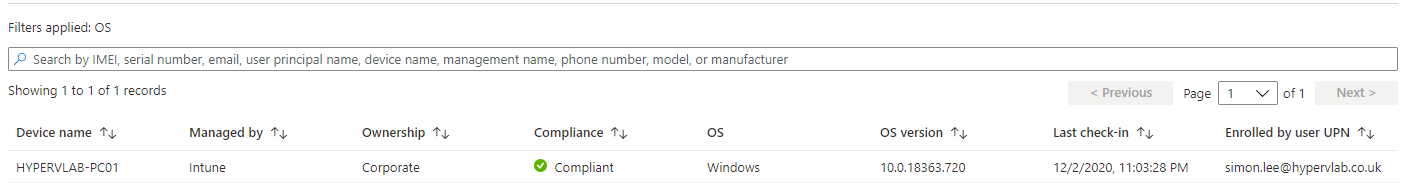
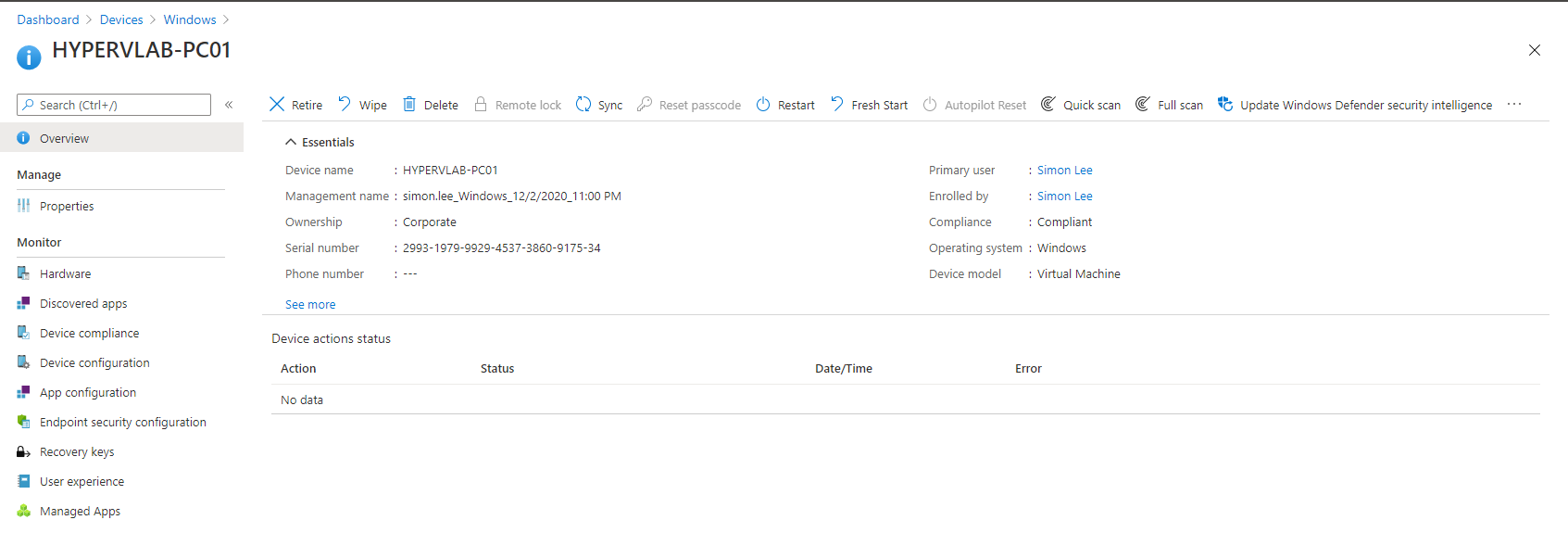
In this blog post, we will cover the steps of a converting a Hybrid Joined Windows Device to an AutoPilot/Intune Enrolled machine. – Firstly this blog post assumes that you already have AzureAD Sync Setup and AzureAD Hybrid Device Sync configured.
For this example, in this lab, we have a computer “HYPERVLAB-PC01” which is a Windows 10 Enterprise Device.
NOTE: If you are struggling to find the device in AzureAD, You might need to force sync from your AzureAD Sync Server. – One thing that I found while creating this post is that the AD Sync wasn’t as fast as I’d liked and took around 15 minutes to catch up and sync the computer into AzureAD.
Hybrid Sync Error – Reference Note
To Check if your device has synced status with AzureAD you can run the command: dsregcmd /status
+----------------------------------------------------------------------+
| Diagnostic Data |
+----------------------------------------------------------------------+
Diagnostics Reference : www.microsoft.com/aadjerrors
User Context : UN-ELEVATED User
Client Time : 2020-12-02 22:25:54.000 UTC
AD Connectivity Test : PASS
AD Configuration Test : PASS
DRS Discovery Test : PASS
DRS Connectivity Test : PASS
Token acquisition Test : SKIPPED
Fallback to Sync-Join : ENABLED
Previous Registration : 2020-12-02 22:24:29.000 UTC
Registration Type : sync
Error Phase : join
Client ErrorCode : 0x801c03f2
Server ErrorCode : DirectoryError
Server Message : The device object by the given id (3c849a08-096e-467c-8eab-b8a3b8f200c0) is not found.
Https Status : 400
Request Id : 49a1e99c-4690-4df9-bffb-630f3698dfa9
Should you get this error message, it means that the device has not synced up to the Azure Tennant, You will need to run a force sync from AzureAD Synchronization Service Manager.
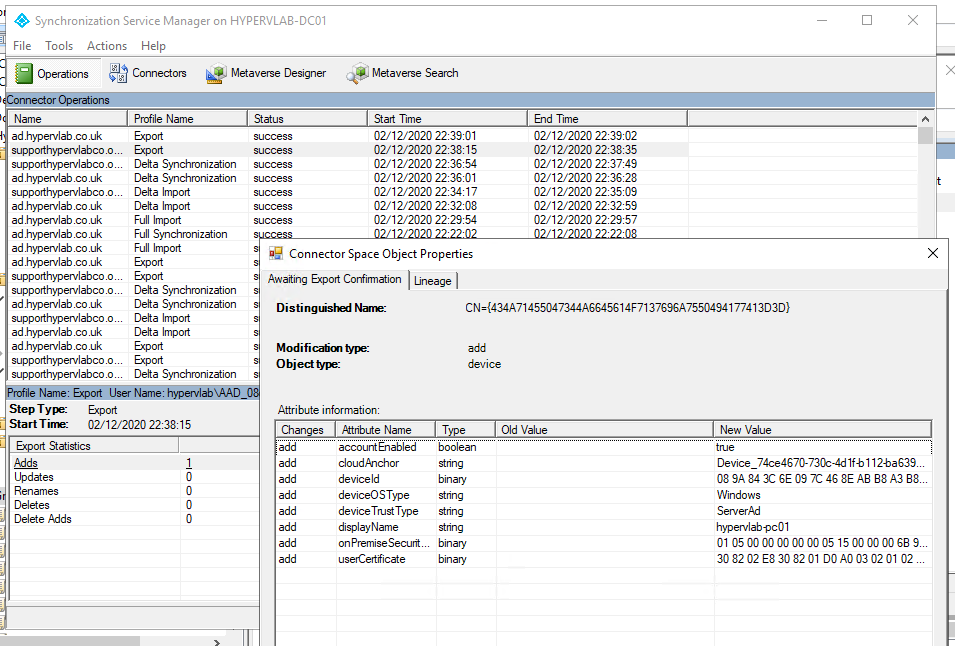
From the reference computer in question, Open Command Prompt as an administrator and run the command:
dsregcmd /join.
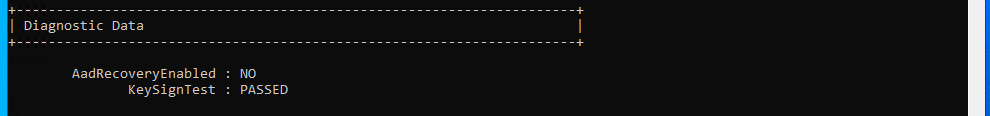
Followed by dsregcmd /status. If the device and checked into AzureAD the Diagnostic Data should report as PASSED.
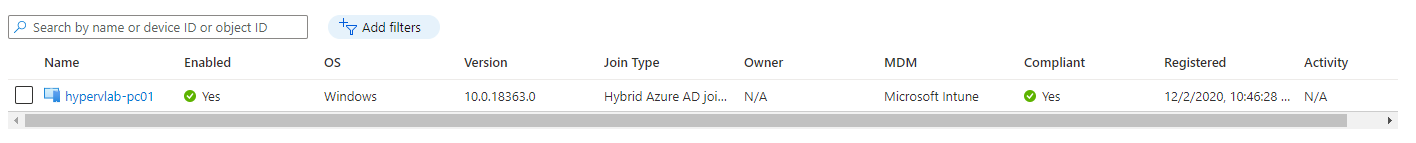
and finally from the AzureAD Portal, under devices you should see the computer in question.
Group Policy – Enable Automatic MDM Enrollment.
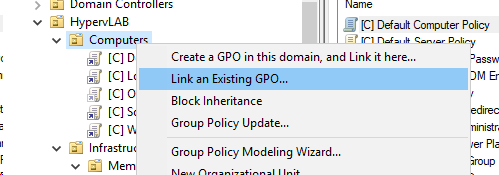
From the Group Policy Management Window, Lets create a new Policy.
Next, lets link the new group policy object to the OU in question “Computers”.
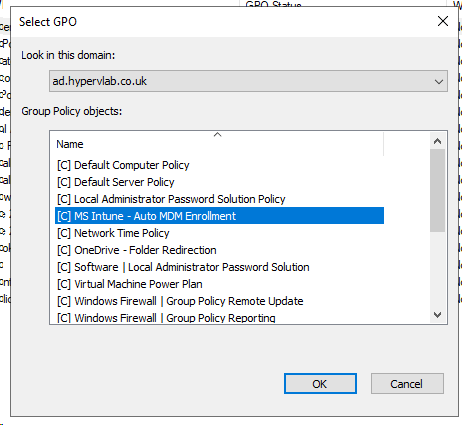
Select the policy we just created “[C] MS Intune – Auto MDM Enrollment.
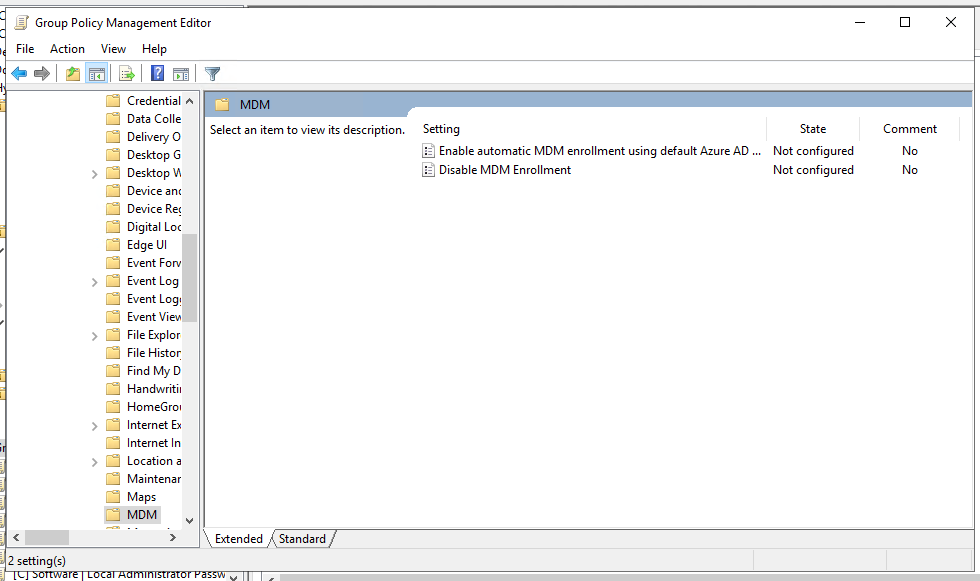
Right-click on the policy and open then Group Policy Management Editor, The Location we are wanting is:
Computer > Polices > Administrative Templates > Windows Components > MDM.
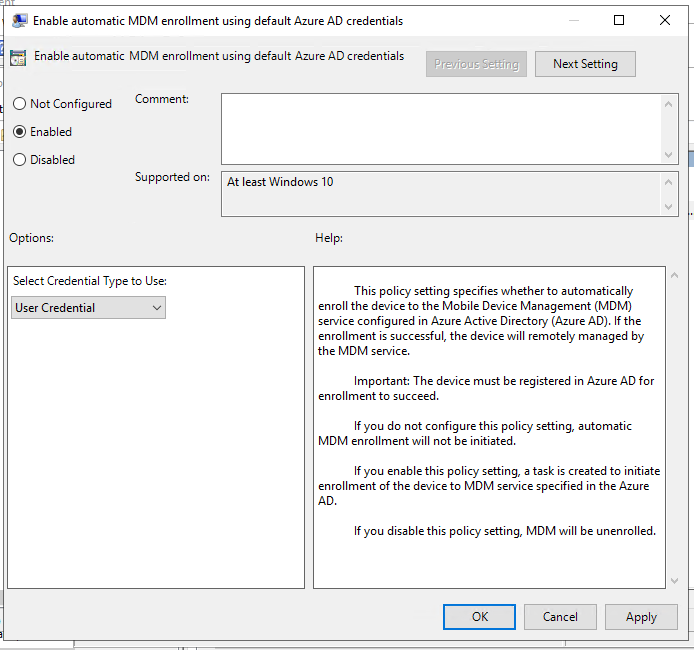
Open the “Enable automatic MDM enrollment using default Azure AD credentials” from the dropdown select “User Credentials” – Trust me on this one, I tried Device Credential and spent two hours debugging and reading event logs!
Once the policy has been configured, we can reboot the reference computer.
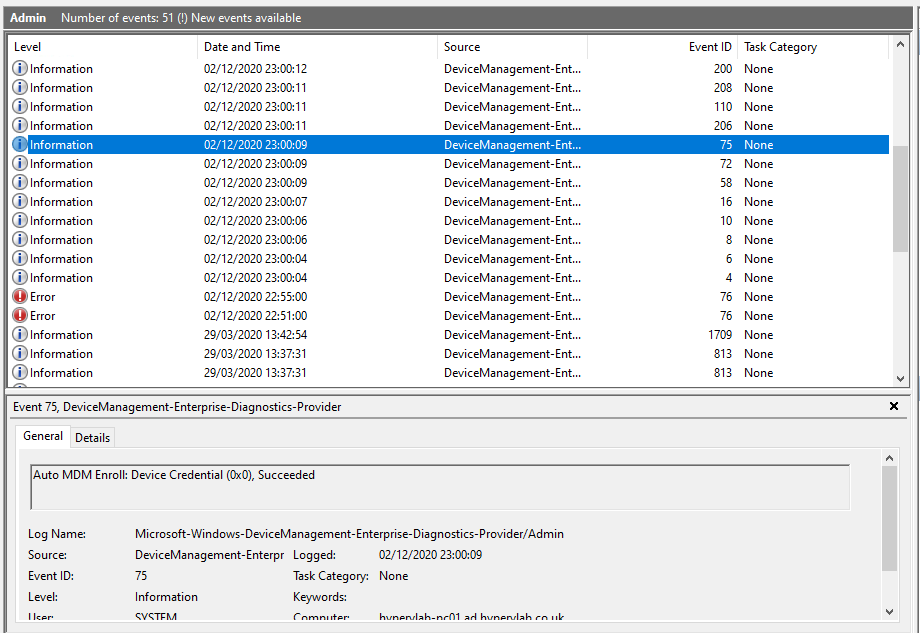
We can check the status on the MDM Enrollment from the Windows Event Viewer (eventvwr.msc)
Applications and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostic-Provider > Admin.
From the Event Viewer logs, If you see an event ID value of “75”. This means that the device is passed the MDM Steps and in now enrollment into Microsoft Intune. If you don’t some further diagnostics is required. [Troubleshooting Steps]
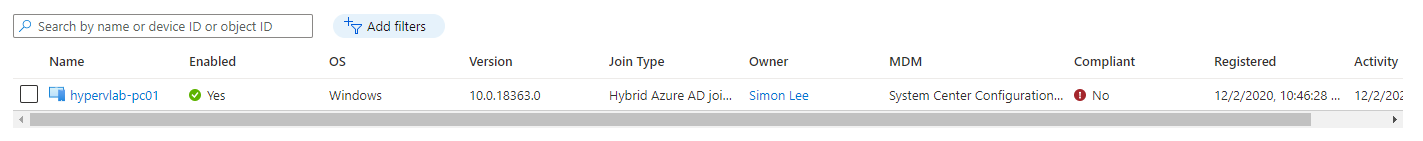
Checking in the AzureAD Devices Portal you will see the device change from a Compliant State to None Compliant.
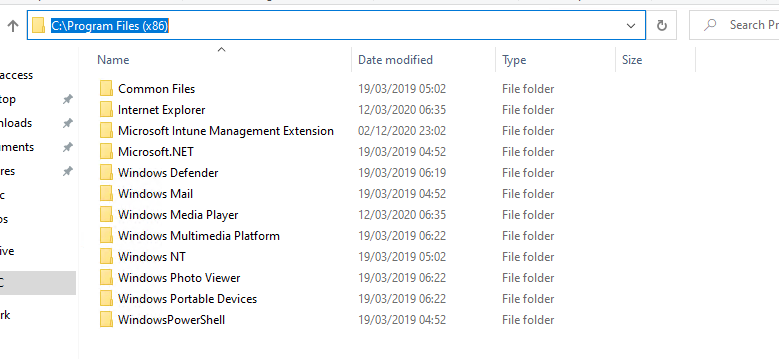
However, checking on the local machine under: C:\Program Files (x86). You should see the Intune Management Extension Folder.
Refreshing the Intune Portal will show the device as “Co-Managed”.
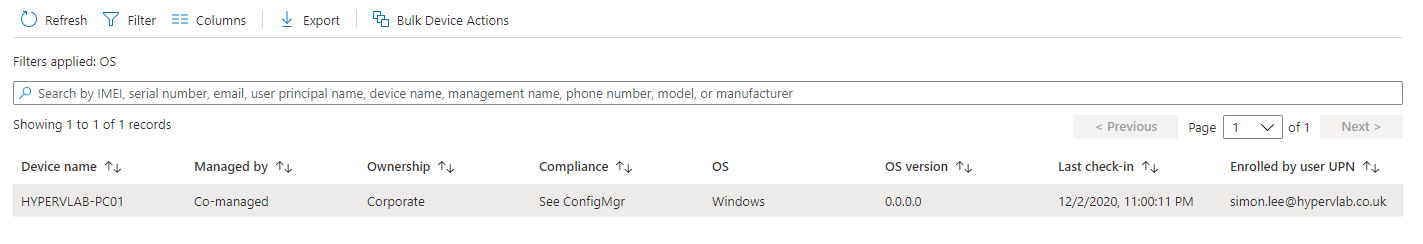
Now its time to grab a coffee, Intune needs to do its thing and complete the sync status and shortly the device will become compliant and be fully enrolled Intune device.