In this blog post, we will cover the steps required to set up. AzureAD Hybrid Sync, in preparation for moving away from our On-Premise Active Directory Server.
Note: This post takes into account that you already have the AzureAD Sync Tool.
Open the Azure Active Directory Connect App – Select “Configure”
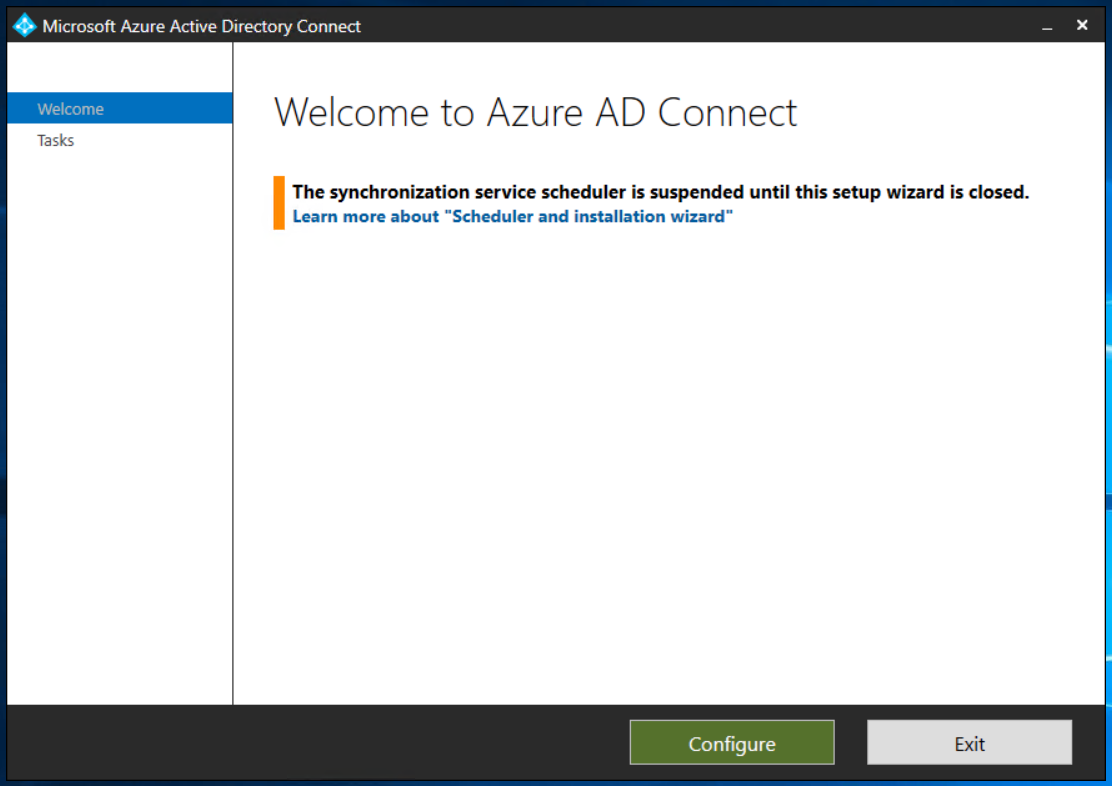
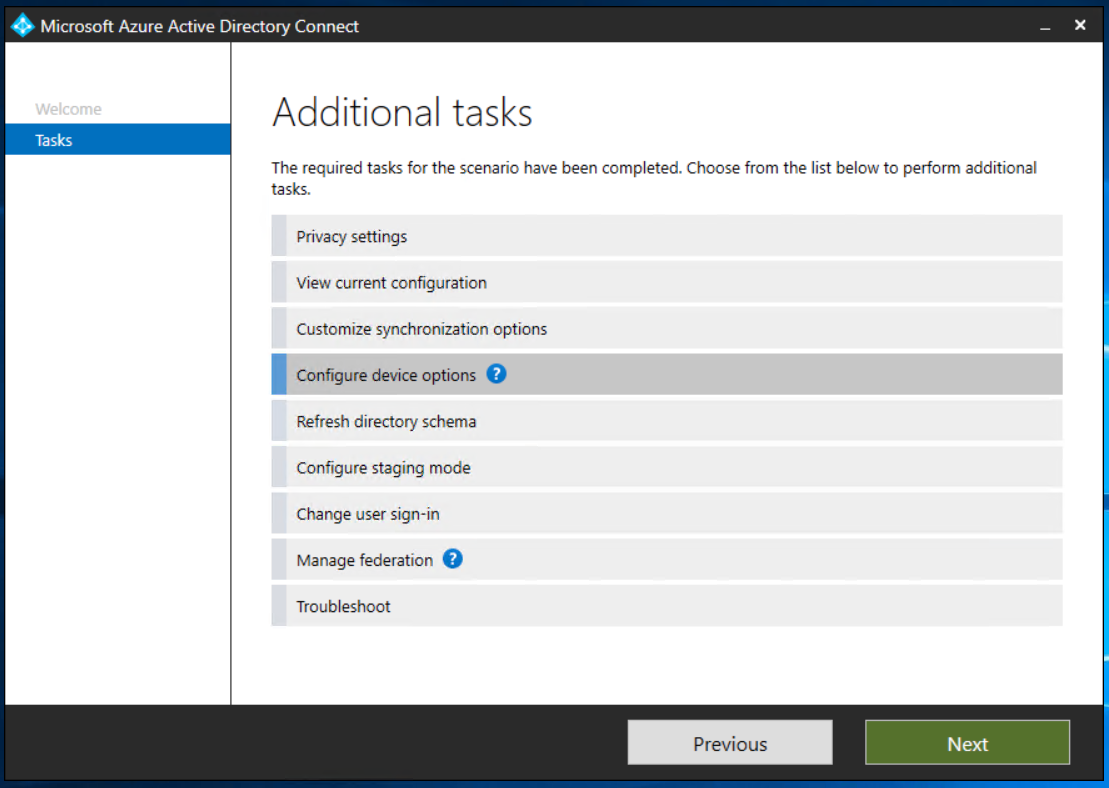
Select “Configure Device Options”
For Hybrid AzureAD Join to work, Your AD Schema needs to be 2012R2 or Higher. For more information, you can check out the Microsoft support documentation [Here]
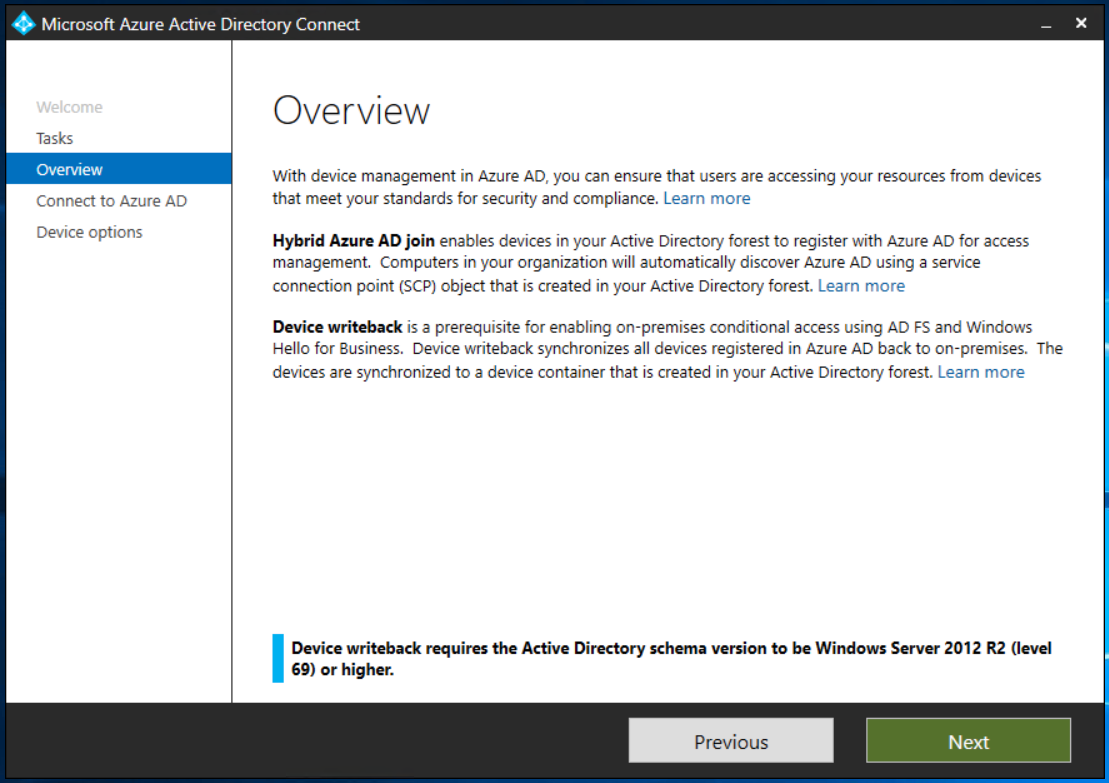
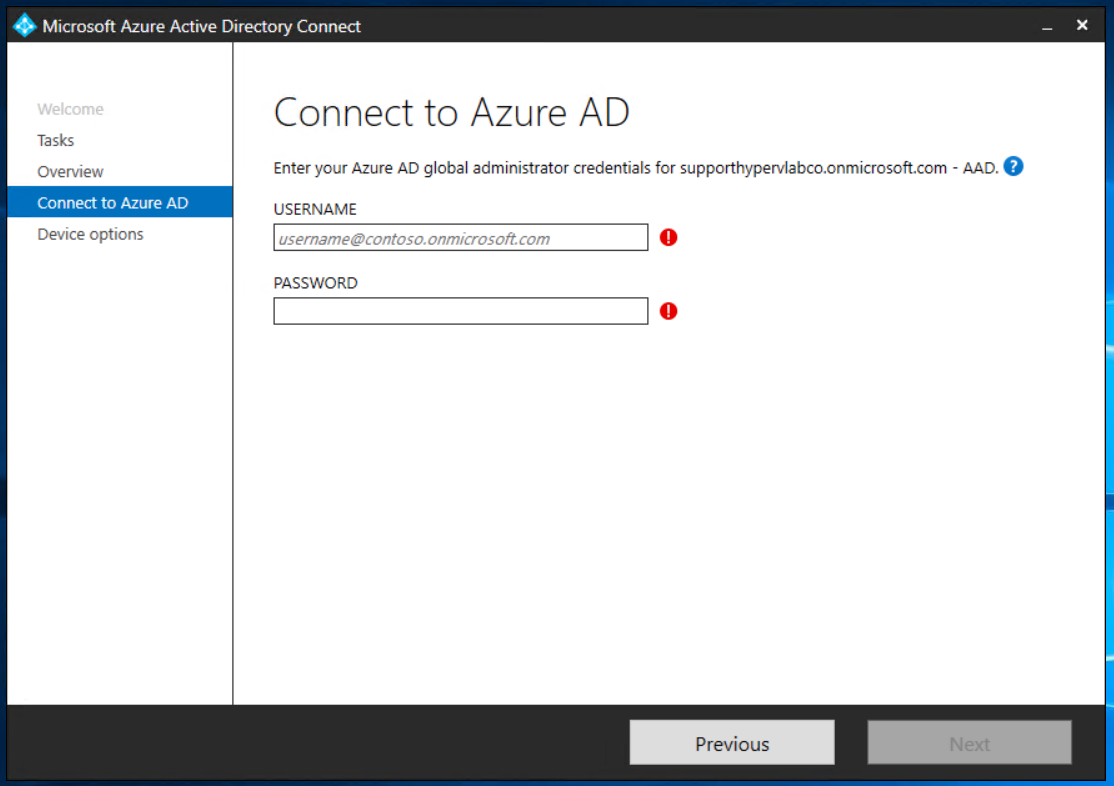
In Connect to Azure AD, enter the credentials of a global administrator for your Azure AD tenant.
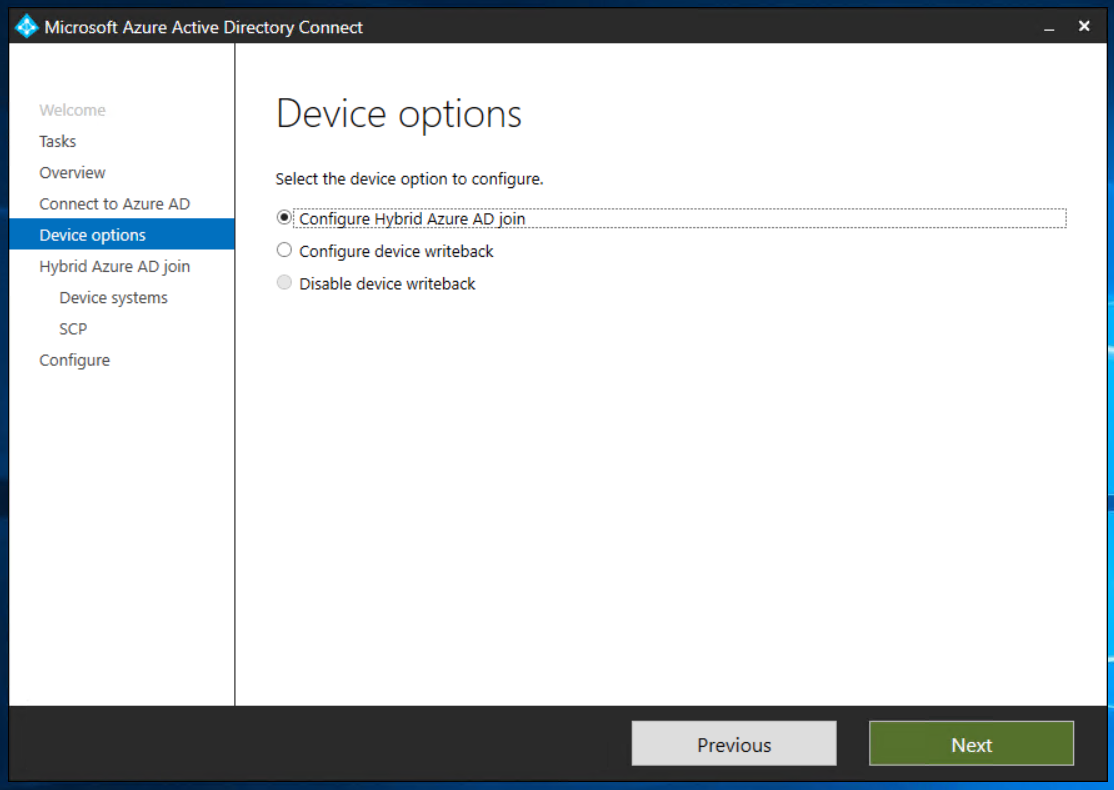
In Device options, select Configure Hybrid Azure AD join, and then select Next.
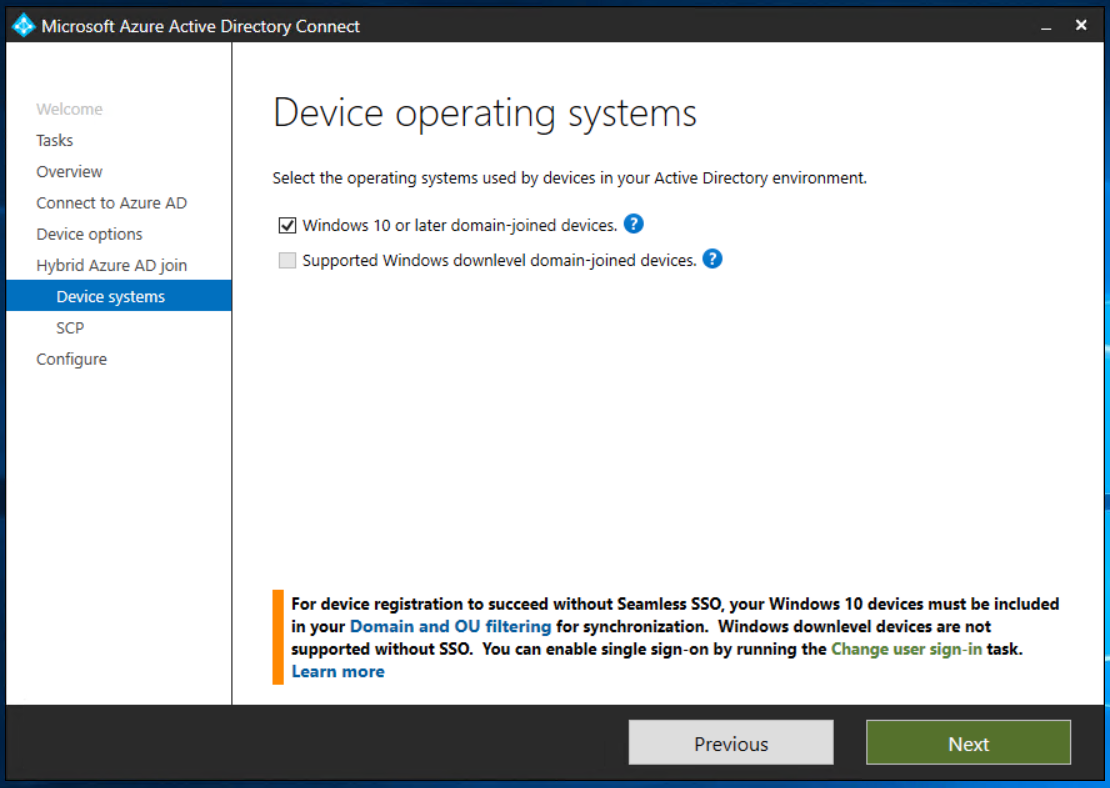
In Device Operating Systems, select the Windows 10 or later domain-joined devices.
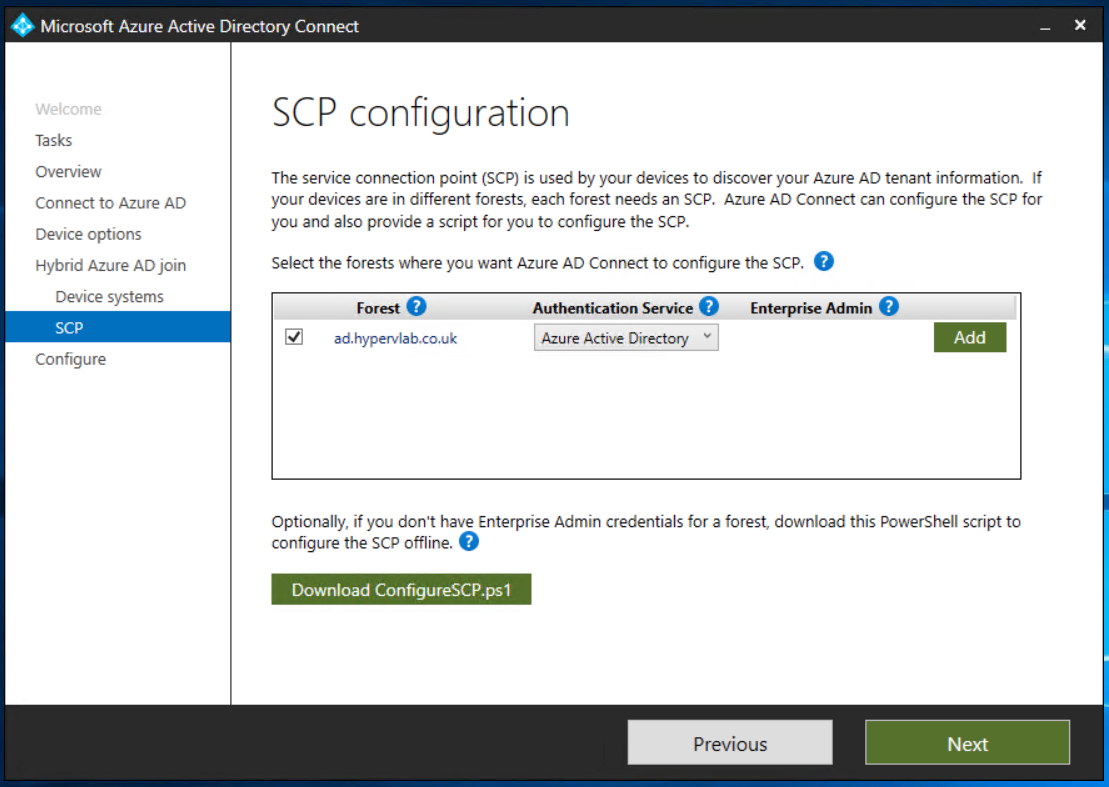
In SCP configuration, for each forest where you want Azure AD Connect to configure the SCP, complete the following steps, and then select Next.
- Select the Forest.
- Select an Authentication Service.
- Select Add to enter the enterprise administrator credentials.
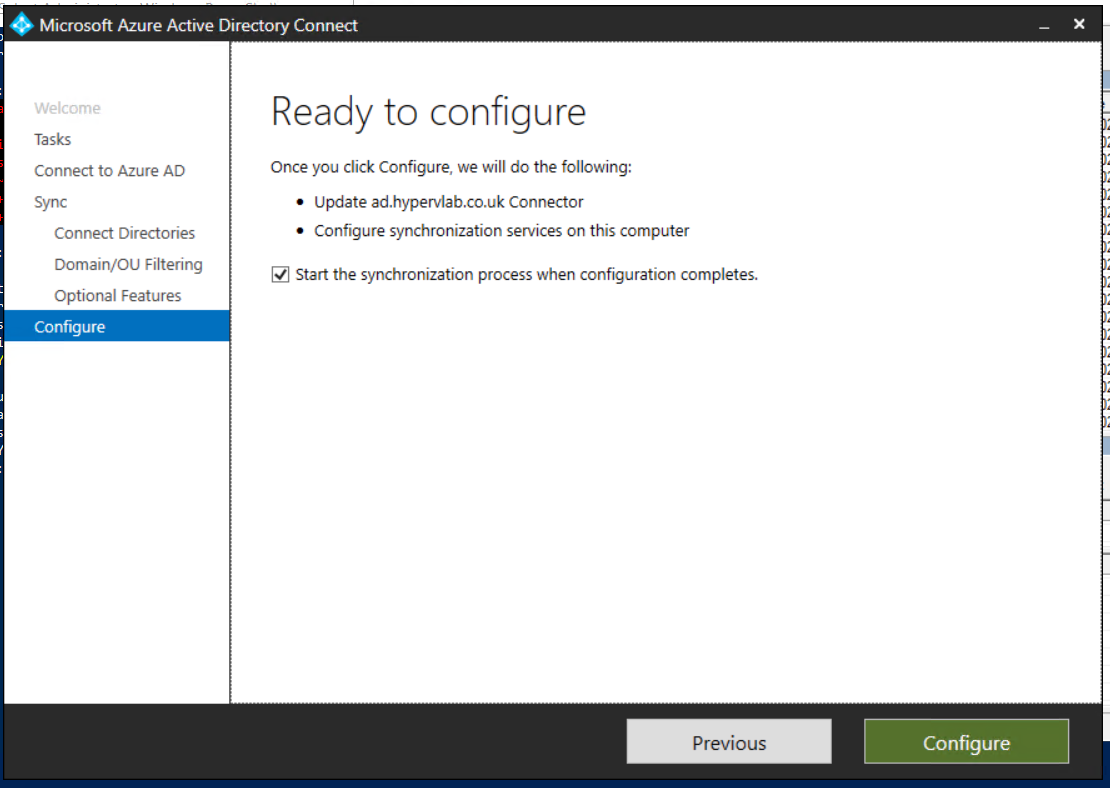
In Ready to configure, select Configure.
Hybrid Domain Join Configuration Completed!
Troubleshooting Hyrbid Join Errors
While testing the steps for the blog post I ran into an error as shown below;
For further diagnostics and support check out the docs.microsoft info: [Here]
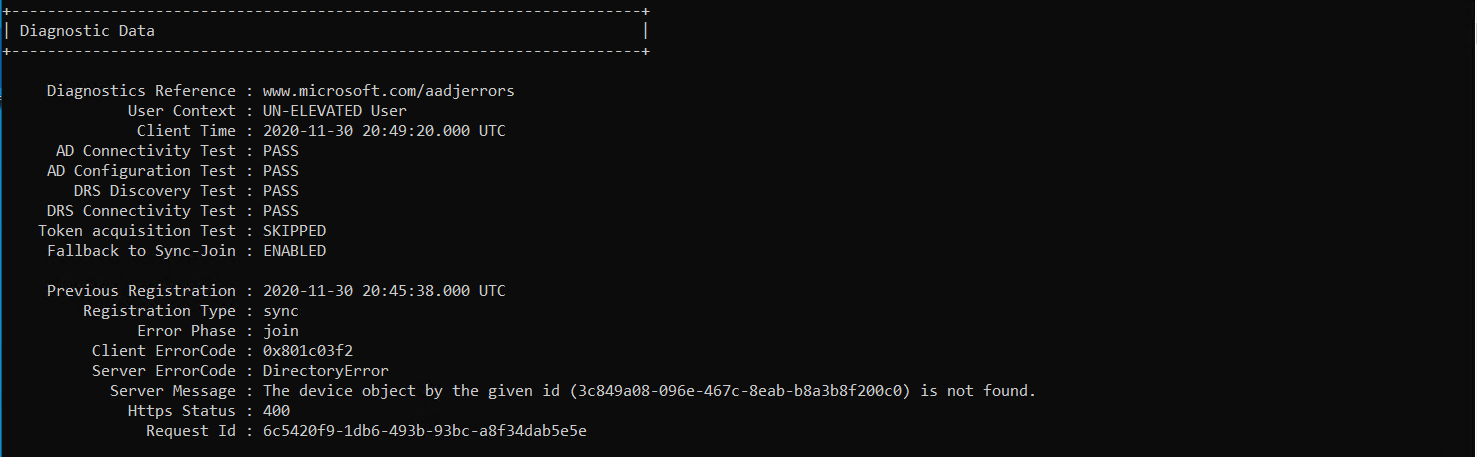
From a look at the event viewer log files it shows.
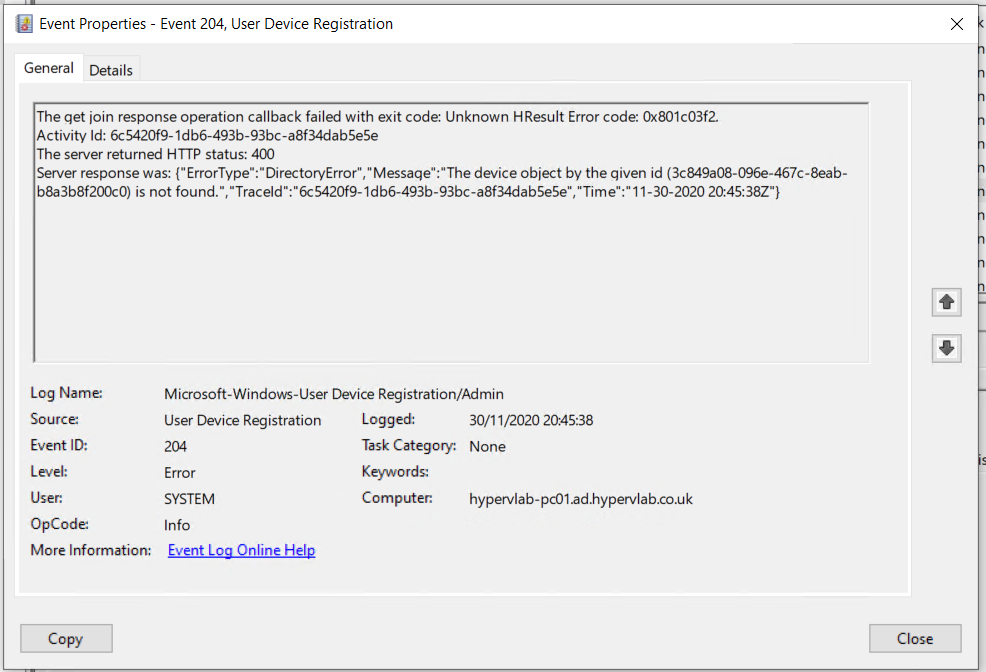
On further investigation, the error message relates to the fact the computer is not found the AzureAD Portal. This means that we’ve missed the OU from the AzureAD Directory Sync.
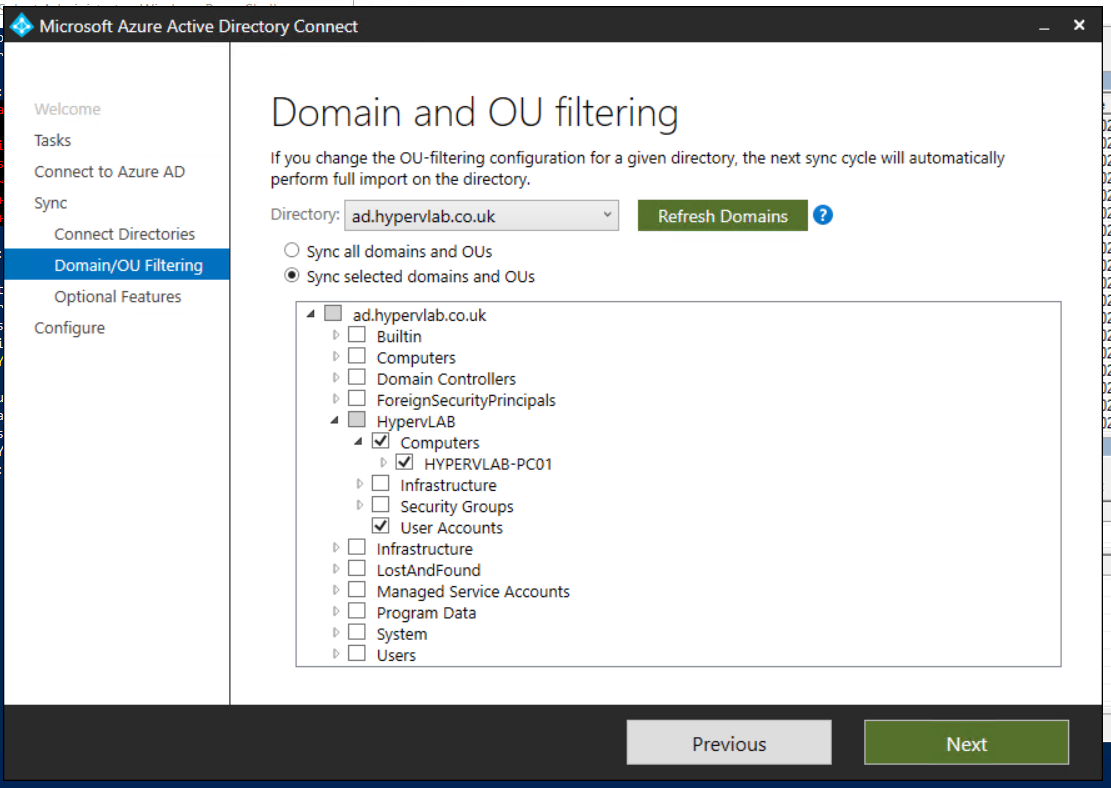
Once the Computer OU has been selected, we can completed an initial sync to AzureAD.
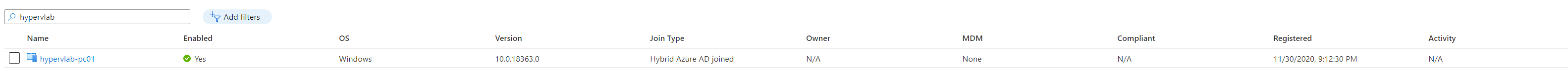
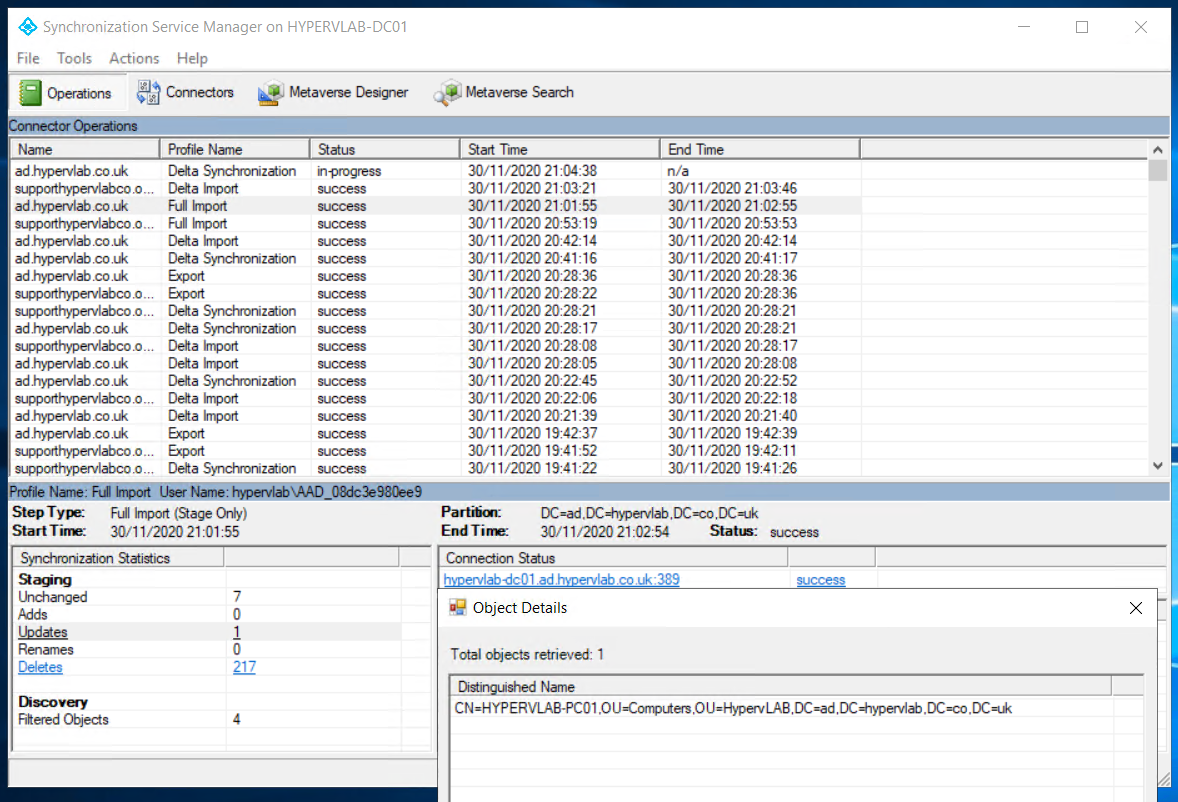
If the sync has been successful you should see a list of computer objects which have been added.
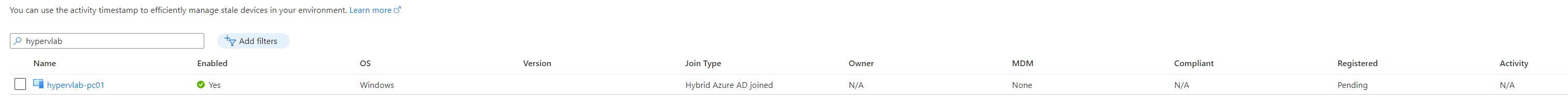
Checking Hybrid Join Status.
From the AzureAD Portal, Under Devices you should see the devices check-in in a “pending” state
From the local machine you can use the command “dsregcmd /status” and get the following result
+----------------------------------------------------------------------+
| Device State |
+----------------------------------------------------------------------+
AzureAdJoined : YES
EnterpriseJoined : NO
DomainJoined : YES
DomainName : hypervlab
+----------------------------------------------------------------------+
| Device Details |
+----------------------------------------------------------------------+
DeviceId : 3c849a08-096e-467c-8eab-b8a3b8f200c0
Thumbprint : 61BBC28FB669FEC1E977FB60ACCCE69DBBAFB0E5
DeviceCertificateValidity : [ 2020-11-30 20:42:30.000 UTC -- 2030-11-30 21:12:30.000 UTC ]
KeyContainerId : 46a23cd7-ac22-4b70-82be-beb6eb0f2a14
KeyProvider : Microsoft Software Key Storage Provider
TpmProtected : NO
+----------------------------------------------------------------------+
| Tenant Details |
+----------------------------------------------------------------------+
TenantName :
TenantId :
Idp : login.windows.net
AuthCodeUrl : https://login.microsoftonline.com/903c83ca-4b31-4b80-baf4-2adcdbed419f/oauth2/authorize
AccessTokenUrl : https://login.microsoftonline.com/903c83ca-4b31-4b80-baf4-2adcdbed419f/oauth2/token
MdmUrl :
MdmTouUrl :
MdmComplianceUrl :
SettingsUrl :
JoinSrvVersion : 1.0
JoinSrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/device/
JoinSrvId : urn:ms-drs:enterpriseregistration.windows.net
KeySrvVersion : 1.0
KeySrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/key/
KeySrvId : urn:ms-drs:enterpriseregistration.windows.net
WebAuthNSrvVersion : 1.0
WebAuthNSrvUrl : https://enterpriseregistration.windows.net/webauthn/903c83ca-4b31-4b80-baf4-2adcdbed419f/
WebAuthNSrvId : urn:ms-drs:enterpriseregistration.windows.net
DeviceManagementSrvVer : 1.0
DeviceManagementSrvUrl : https://enterpriseregistration.windows.net/manage/903c83ca-4b31-4b80-baf4-2adcdbed419f/
DeviceManagementSrvId : urn:ms-drs:enterpriseregistration.windows.net
+----------------------------------------------------------------------+
| User State |
+----------------------------------------------------------------------+
NgcSet : NO
WorkplaceJoined : NO
WamDefaultSet : NO
+----------------------------------------------------------------------+
| SSO State |
+----------------------------------------------------------------------+
AzureAdPrt : NO
AzureAdPrtAuthority :
EnterprisePrt : NO
EnterprisePrtAuthority :
+----------------------------------------------------------------------+
| Diagnostic Data |
+----------------------------------------------------------------------+
AadRecoveryEnabled : NO
KeySignTest : PASSED
+----------------------------------------------------------------------+
| Ngc Prerequisite Check |
+----------------------------------------------------------------------+
IsDeviceJoined : YES
IsUserAzureAD : NO
PolicyEnabled : NO
PostLogonEnabled : YES
DeviceEligible : NO
SessionIsNotRemote : NO
CertEnrollment : none
PreReqResult : WillNotProvision
Finally going back to the AzureAD Device Portal we can see that the device has completed the check-in